When building secure web applications, choosing the right authentication mechanism is crucial.
Today, we’re exploring two widely used approaches: session-based authentication and JSON Web Tokens (JWTs). By understanding their workflows, advantages, and trade-offs, you’ll be equipped to decide which one suits your application best.
Table of contents
Open Table of contents
What is Session-Based Authentication and How Does It Work?
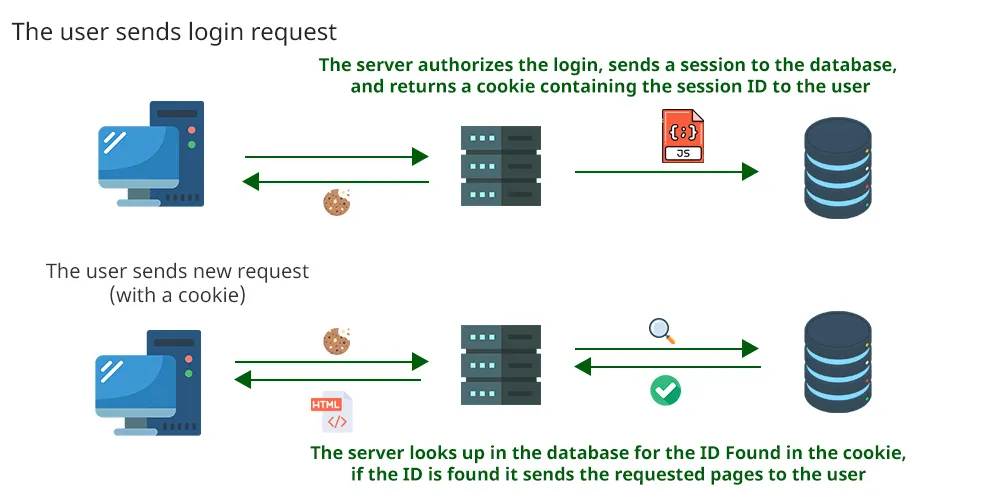
Here’s how session-based authentication works:
-
Login and Session Creation:
- The user sends login credentials to the server.
- The server verifies them and, if valid, creates a session.
- Session data (e.g., user ID, expiration time) is stored on the server in a database or cache like Redis.
-
Session ID:
- The server sends a unique session ID to the client, usually as a cookie.
-
Subsequent Requests:
- The client automatically sends the session ID cookie with each request.
- The server uses this ID to retrieve session data and authenticate the user.
Key Benefits
- Easy Revocation: A session can be invalidated anytime by deleting the session data.
- Centralized Security: Sensitive information stays on the server.
Challenges
- Distributed Systems: In multi-server environments, all servers need access to the same session data, requiring a centralized session store like Redis.
- Added Latency: Fetching session data adds overhead to each request.
What is JWT Authentication and How Does it Work?
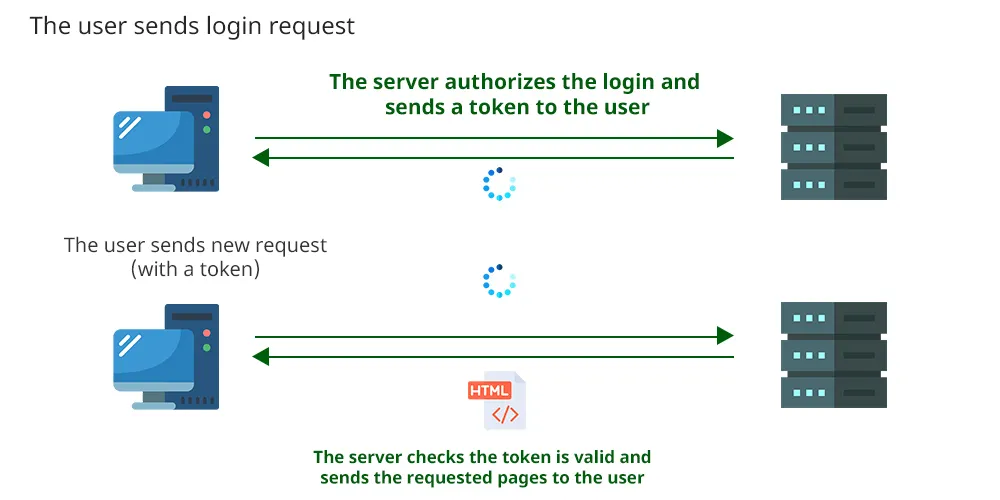
JWTs take a different approach:
-
Login and Token Generation:
- The user sends login credentials to the server.
- The server verifies them and generates a signed JWT containing user data.
- The client stores the JWT (e.g., in local storage or a cookie).
-
Subsequent Requests:
- The client sends the JWT in request headers.
- The server verifies the token’s signature and uses its data for authentication.
Key Benefits
- Stateless and Scalable: No session data is stored on the server, making JWTs ideal for horizontally scalable applications.
- Inter-Service Compatibility: In microservice architectures, services can trust the data in a verified JWT without querying the authentication service.
Challenges
- Token Expiration: If stolen, a JWT is valid until it expires.
- Security Trade-Offs: The server must implement mechanisms like refresh tokens to improve security.
Choosing the Right Signing Algorithm
- HMAC: A symmetric key is used for signing and verification. Simple but requires sharing the key, which may pose risks.
- RSA/ECDSA: Asymmetric keys ensure the private key signs tokens while the public key verifies them, enhancing security for distributed systems.
When to Use Each Method?
Session-Based Authentication
- Ideal when you need immediate session revocation.
- Suited for applications with a centralized data store.
- Keeps sensitive data on the server, enhancing security.
JWT-Based Authentication
- Best for stateless, scalable architectures.
- Useful in microservices or when sharing authentication data with third-party services.
- Pair JWTs with refresh tokens for a balance of security and user experience.
Ultimately, your choice depends on your application’s architecture, scaling requirements, and security needs. Whether you go with sessions or JWTs, understanding these mechanisms ensures a secure and seamless user experience.